Create a Static IP, VPC and Firewalls for Stream Manager Instance
Creating a Static IP for Stream Manager Instance in GCP
-
Go to the VPC network page in the Google Cloud Console.
-
In the VPC Network section, click on IP Addresses in the left-hand menu → click on Reserve External Static IP address.
-
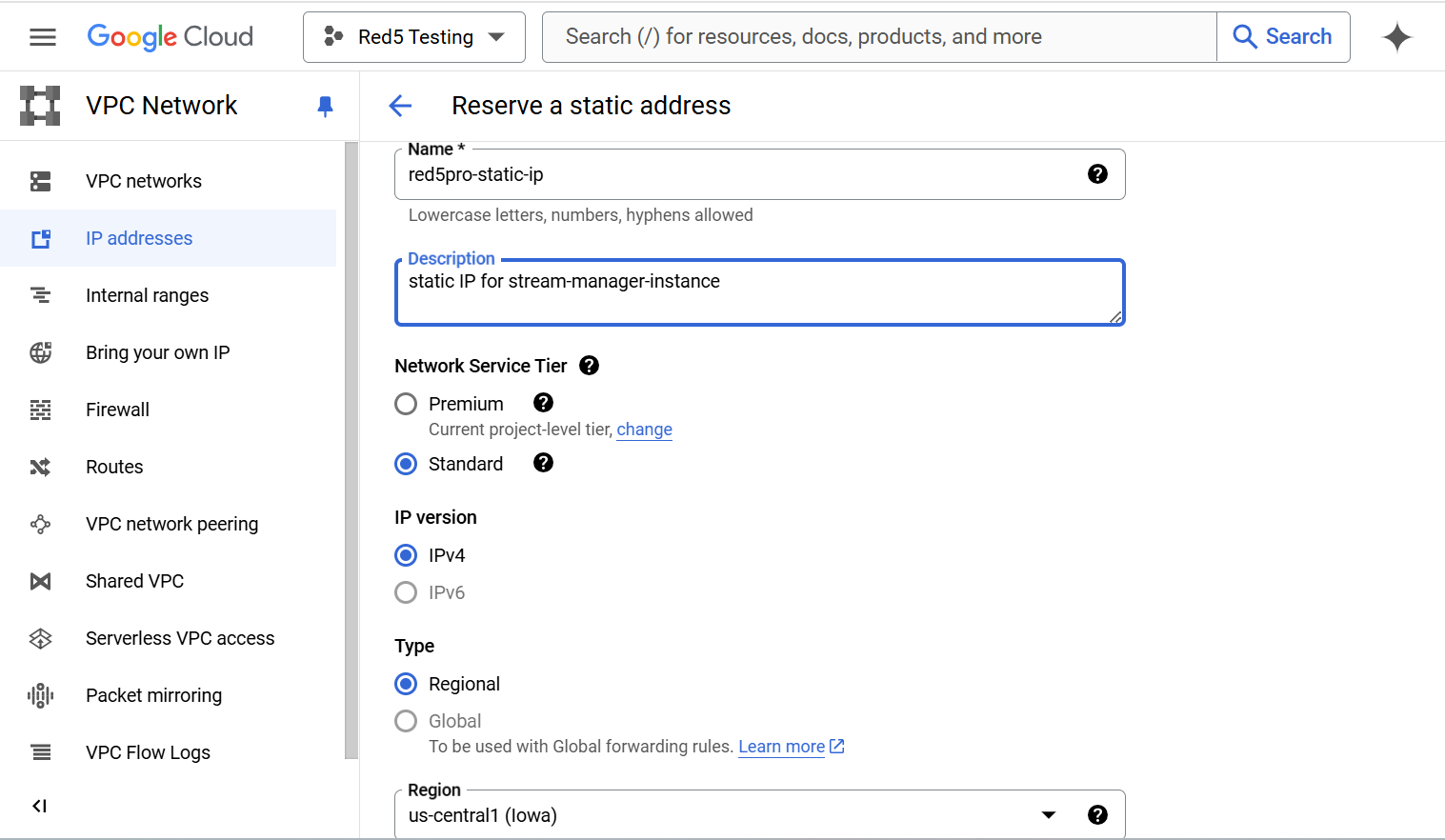
Enter a name for the static IP address, such as
red5pro-static-ip. -
Under Network tier, select Standard.
-
Select the appropriate IP version Click checkbox
IPv4 and IPV6is typically used for Stream Manager). -
Choose the Regional type, Where the Stream Manager instance will be deployed. In
regionfield select a location, For Exampleus-central1 -
Click Reserve to create the static IP address.
After the static IP is reserved, it will be listed under External IP addresses. This IP can now be associated while the usage of Stream Manager instance.
Creating a Network for Stream Manager Instance
-
Go to the VPC networks page in the Google Cloud Console.
-
Click the Create VPC network button.
-
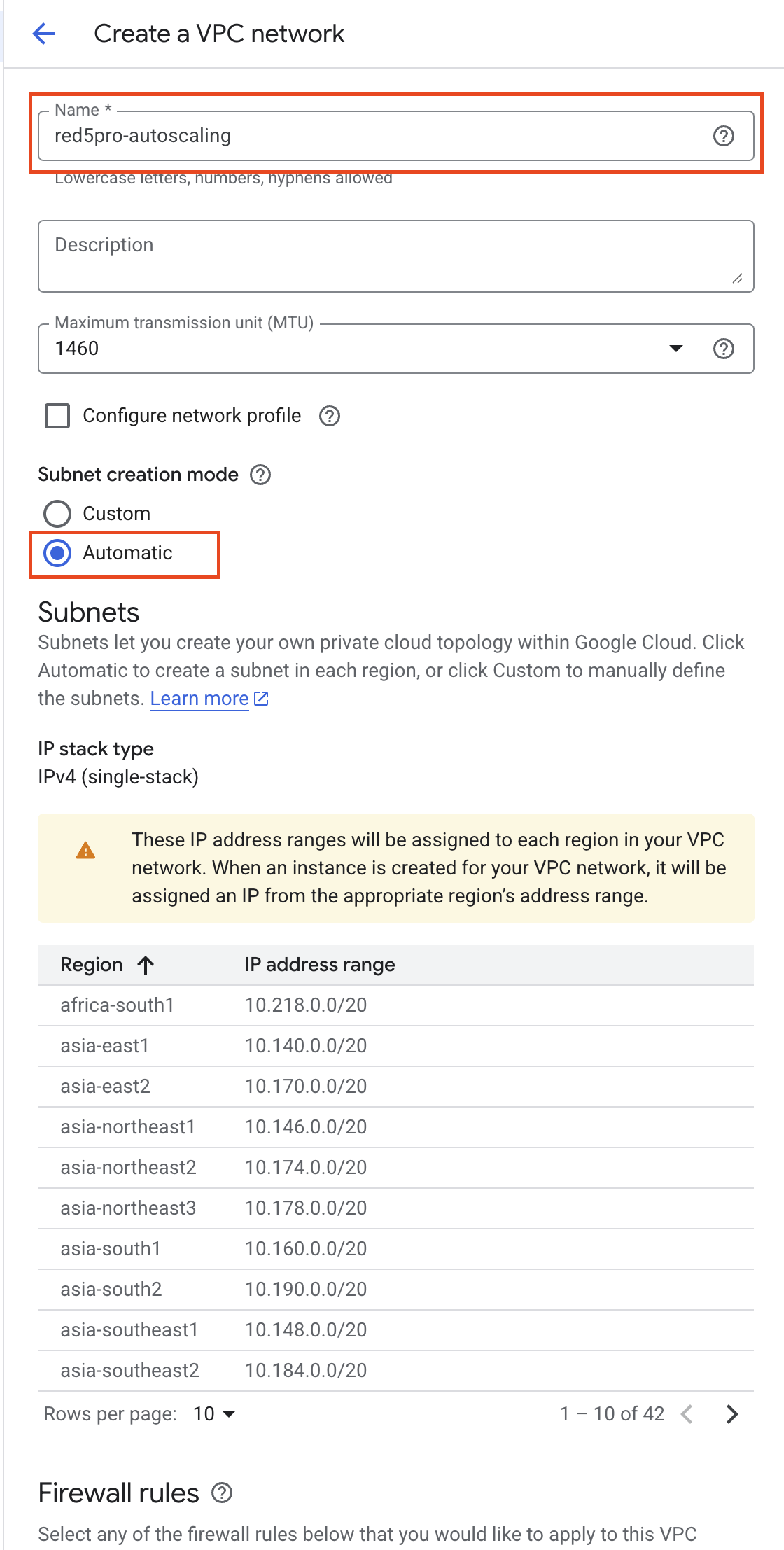
Enter a name for the network, such as
red5pro-autoscalingand MTU value as1460. -
Under Subnet creation Mode → select Automatic.
⚠️ Stream Manager 2.0 currently requires Automatic subnet mode for proper operation.
-
At the bottom, Click on Create button.
Please record VPC name and Region to your checklist for the NODE_VPC_NAME, NODE_GCP_REGION parameters, it will be using in API calls to Stream Manager to create node group config.
The new network is now ready to be associated with the Stream Manager instance and the reserved static IP.
Create Firewalls for GCP
We need to create 2 firewall rules:
- Firewall rule for Stream Manager instance
- Firewall rule for Red5 Pro nodes
Firewall Rule for Stream Manager
Go to Google Cloud Console → VPC network →Firewall rules.
- Click on Create firewall rule.
- Name:
red5pro-autoscaling-sm-sg - Network: Select the VPC you created (e.g.,
red5pro-autoscaling). - Set Direction of traffic to Ingress.
- Set Action on match to Allow.
- Under Targets, choose
All instances in the networkor select the specific instance tags if you are using them. - Set Source filter to IP ranges, and set the Source IP ranges as
0.0.0.0/0for IPv4 and::/0for IPv6 for the desired rules. - Add Protocols and ports to allow the required traffic:
| Name | Protocol | Port Range | Source IPs | Description |
|---|---|---|---|---|
| HTTP Rule (IPV4) | TCP | 80 | 0.0.0.0/0 | HTTP |
| HTTPS Rule (IPV4) | TCP | 443 | 0.0.0.0/0 | HTTPS |
| Kafka Rule (IPV4) | TCP | 9092 | 0.0.0.0/0 | Kafka |
| HTTP Rule (IPv6) | TCP | 80 | ::/0 | HTTP (IPv6) |
| HTTPS Rule (IPv6) | TCP | 443 | ::/0 | HTTPS (IPv6) |
| Kafka Rule (IPv6) | TCP | 9092 | ::/0 | Kafka (IPv6) |
- Click on Create.
Firewall Rule for Red5 Pro Nodes
Go to Google Cloud Console → VPC network → Firewall rules.
- Click on Create firewall rule.
- Name:
red5pro-autoscaling-node-sg - Network: Select the same VPC you created (e.g.,
red5pro-autoscaling). - Set Direction of traffic to Ingress.
- Set Action on match to Allow.
- Under Targets, choose
All instances in the networkor select the specific instance tags if you are using them. - Set Source filter to IP ranges, and set the Source IP ranges as
0.0.0.0/0for IPv4 and::/0for IPv6 for the desired rules. - Add Protocols and ports to allow the required traffic:
| Name | Protocol | Port Range | Source IPs | Description |
|---|---|---|---|---|
| HTTP Rule (Port 5080) | TCP | 5080 | 0.0.0.0/0 | HTTP (IPV4, Port 5080) |
| HTTP Rule (Port 1935) | TCP | 1935 | 0.0.0.0/0 | HTTP (IPV4, Port 1935) |
| TURN/STUN/ICE (IPV4) | UDP | 40000-65535 | 0.0.0.0/0 | TURN/STUN/ICE |
| HTTP Rule (Port 5080, IPv6) | TCP | 5080 | ::/0 | HTTP (IPv6, Port 5080) |
| HTTP Rule (Port 1935, IPv6) | TCP | 1935 | ::/0 | HTTP (IPv6, Port 1935) |
| TURN/STUN/ICE (IPv6) | UDP | 40000-65535 | ::/0 | TURN/STUN/ICE (IPv6) |
- Click on Create.
Outbound Rules for Both Stream Manager and Red5 Pro Nodes
In GCP, Firewall rules are typically used for inbound traffic (ingress). Outbound traffic (egress) is allowed by default. However, you can customize outbound rules if necessary.
To allow all outbound traffic:
-
Outbound Rule for All Traffic:
- Name:
red5pro-all-outbound - Network: Select your existing VPC from previous steps.i.e;
red5pro-autoscaling - Direction of traffic: Egress
- Action on match: Allow
- Destination filter:
0.0.0.0/0for IPv4 and::/0for IPv6. - Protocols and ports: Select All traffic.
- Name:
-
Click on Create.
Please record the Firewall Rule name for Red5 Pro nodes in your checklist for the
NODE_SECURITY_GROUPparameter, as it will be used in API calls to Stream Manager to create node group configurations.